Labyrinth detects and responds to hacking activities, defending core assets from compromise.
Using deception technology, our Platform provides security teams with a simple and efficient tool for the earliest possible detection of attackers inside corporate networks.
- Intrusion Detection : Unauthorized Access, Vulnerabilities Exploitation, Command-and-Control attacks
- Data Gathering and Analysis: Threat identification, Pattern analysis, Content analysis
- Automated Response: Generation of threat indicators, Isolation of compromised hosts, Incident Logging and Reporting
Labyrinth Solution Description
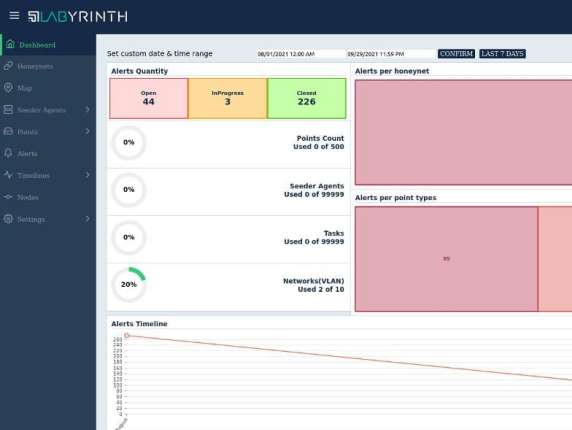
DownloadReasons to enhance your cyber defense with Labyrinth
next-gen deception platform focused on intrusion detection
Hacking activities prevention
51% of all detected intrusion attempts into information systems is malware-free attacks
Silent failure detection
56% of breaches aren’t discovered for at least a matter of months
Valuable assets protection
60% of businesses have experienced a serious security breach in the last two years
Don't just take our word for it
Company Reviews and Ratings on gartner.com


Shift detection left!
Cybercriminals continue to become more advanced and sophisticated. Traditional security measures, such as firewalls and endpoint protection, are insufficient to stop hackers and protect sensitive data from leakage. Solutions for early intrusion detection in corporate IT networks are crucial for defending organizations against today’s adversaries.
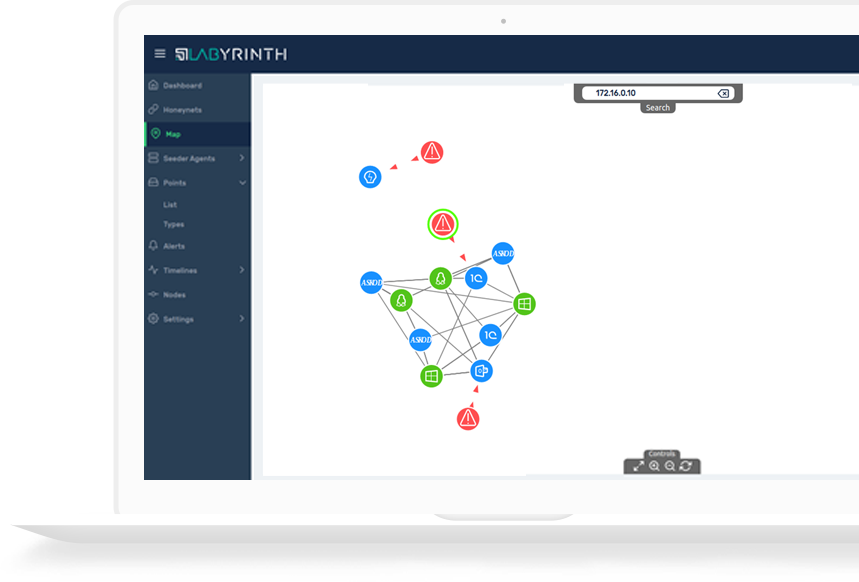

Why Labyrinth
Labyrinth provides adversaries with an illusion of IT services and applications vulnerabilities to provoke them for actions, detects and monitors all their activities, and isolates them from real IT network.
- NO long implementation process Simple installation and configuration - ready to work in hours, not days
- NO terabytes of data to store The Platform gathers only valuable data related to security incidents
- NO overwhelming security alerts The solution is silent until it is being touched, so does not generate “digital noise”
- NO false-positive warnings Labyrinth provides security teams with highly reliable alerts with less than 1% false positives
- NO special skills needed Intuitive interface provides full real-time attack visibility
Labyrinth’s unique features ensure the protection of your applications and services on-premise and in the cloud.
Extended detection capabilities
The Platform provides attackers with a broad range of fake application and service vulnerabilities to increase the attack surface and ensure all the possible attack vectors covering.
Advanced WEB application protection
Labyrinth embedded a unique technology which allows providing additional leer of security for the most desired by hackers target – WEB based applications and services.
Active Defense
Client Honeypots are active security devices using for search of malicious servers attacking clients and MITM detection. They pose as a client and check whether an attack has occurred.
LabyrinthDeception Platform provides you with

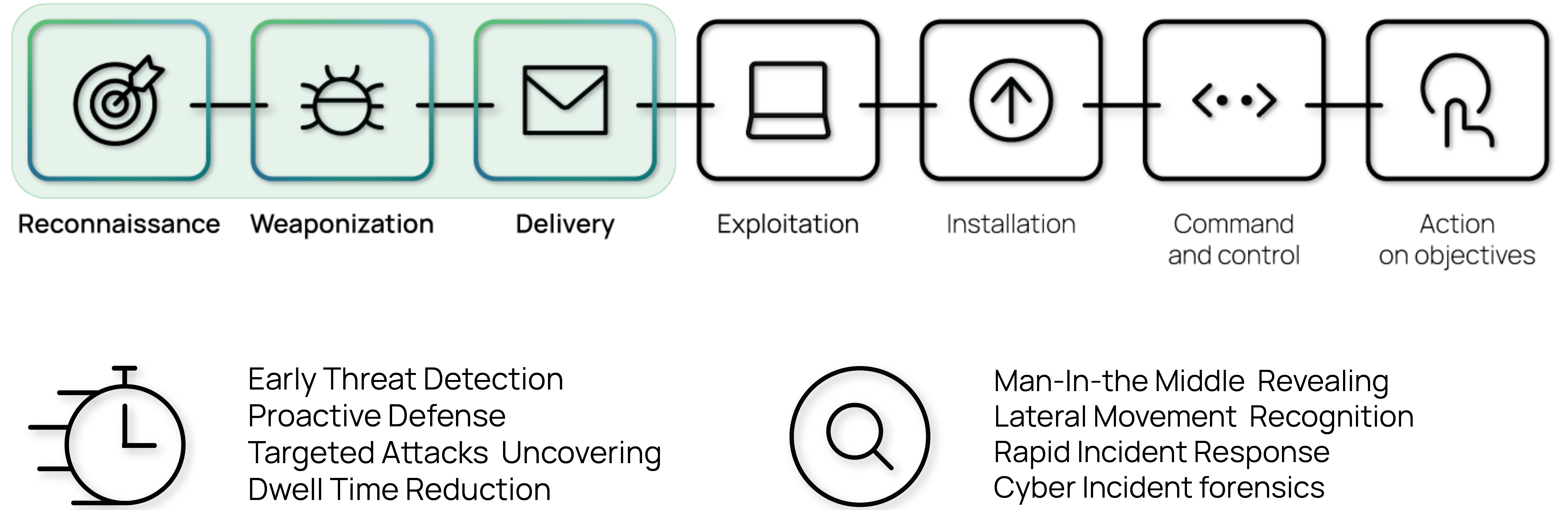
Early Intrusion Detection
Labyrinth designed to catch threat actions when an attacker tries to understand the network architecture and to find its target. Once an attacker has been detected, the platform gathers all the details about them: the threat sources, the tools used, and vulnerabilities exploited.

Targeted Attacks Uncovering
Labyrinth lures hackers into a false sense of security and allows to learn their skillset and motives. Awareness of what attackers know about company networks, applications, and employees help to create the most accurate profile of attackers and apply the best possible way to defend against them.

Rapid Incident Response
All gathered by Labyrinth events are enriched with necessary security data from the Incident Response Platform. Indicators of Compromise (IoC) generated by Labyrinth automatically synchronize to Threat Prevention Solutions. It allows in case of attack to take action immediately.
Post Infection Detection
Labyrinth serves as a highly reliable alerting system of attacks that have bypassed perimeter security controls. Agents, deployed on servers and workstations, mimic the most “delicious”, for an attacker, artifacts. What appears to be a high-privilege and badly protected administrator account is a trap that entices an attacker to Labyrinth.

Lateral Movement Recognition
In the phase of lateral movement, an attacker moves in a company network from one asset to another. Labyrinth is designed to detect early reconnaissance, credential theft, and lateral movement. The Platform allows companies to gain such threats visibility at their early stage that is a complicated task for traditional security solutions.

Dwell Time Reduction
Labyrinth detection mechanism is especially efficient for reducing dwell time, which is a crucial condition for an attacker to successfully complete an attack. Labyrinth reduces dwell time and ability for attackers to move inside companies' networks and stops them before they reach critical assets and services.
We are recognized by PCSI as an organization that shares the goals and vision of PCSI, and we are eagerly interested in learning and contributing to current and future innovations in the field of cybersecurity!
PCSI
pcsi.nl
We are recognized as a member of the ECSO organization, and we contribute to the development of cybersecurity communities and the creation of a European cybersecurity ecosystem!
ECSO
ecs-org.eu



