Labyrinth Security Solutions Announces Strategic Partnership with SecuVerse.AI as Official VAD for Africa
Zabrze, Poland - February, 3 - Labyrinth Security Solutions, a global leader in proactive, deception-based cybersecurity, is excited to announce a new strategic partnership with SecuVerse.AI, which...
Labyrinth Security Solutions and A.B. Distributing, Inc. Partner to Deliver Advanced Cybersecurity Solutions in the United States
Zabrze, Poland — January, 6 — Labyrinth Security Solutions is pleased to announce a new strategic partnership with A.B. Distributing, Inc., which now becomes Labyrinth’s Value-Add...
Labyrinth Security Solutions Welcomes Cyberrey as New Value-Added Distribution Partner
Zabrze, Poland — November, 19 – Labyrinth Security Solutions is pleased to announce a new strategic partnership with Cyberrey, a growing Value-Added Distributor (VAD) dedicated to deliv...
Labyrinth Security Solutions Welcomes OneDot61 as New Value-Added Distribution Partner for Australia and New Zealand
Zabrze, Poland — August 14, 2025 – Labyrinth Security Solutions is pleased to announce a new strategic partnership with OneDot61, a leading value-added distributor specializing in innov...
Labyrinth Security Solutions and Mondist Partner to Deliver Advanced Cybersecurity Solutions in Serbia
Zabrze, Poland — July 10, 2025 — Labyrinth Security Solutions is proud to announce a strategic partnership with Mondist, a respected Value-Added Distributor of IT infrastructure and cyb...
Release notes v2.2.0
We're excited to announce the release of the new Labyrinth Deception Platform version: v2.2.0! This latest version introduces powerful new features and enhancements designed to make Labyri...
Labyrinth Security Solutions Partners with Neogenesys to Expand Presence in Latin America
Zabrze, Poland — June 24, 2025 — Labyrinth Security Solutions is pleased to announce a strategic partnership with Neogenesys, a leading cybersecurity distributor headquartered in Mexico...
Labyrinth Partners with COMPUTER 2000 to Deliver Advanced Cybersecurity Solutions in Bulgaria
Zabrze, Poland / Sofia, Bulgaria — May 28, 2025 — Labyrinth Security Solutions, a leading provider of deception-based cybersecurity technologies, is pleased to announce the partnership ...
LABYRINTH and Serviceware Announce Strategic Partnership for Germany, Austria, and Switzerland
Zabrze, Poland, April 20, 2025 – LABYRINTH, a European leader in proactive cybersecurity solutions, is pleased to announce its partnership with Serviceware, a trusted provider of enterprise s...
LABYRINTH Partners with CLOUDS DUBAI as Value-Added Distributor in the Middle East
Zabrze, Poland, April 10, 2025 — LABYRINTH SECURITY SOLUTIONS, a leading provider of deception-based intrusion detection systems, is pleased to announce the appointment of Clouds Dubai as its...
Labyrinth Recognized as a Strong Performer in the Cyberhive Matrix Q1 2025
The cybersecurity landscape is evolving rapidly, making independent, transparent evaluations more crucial than ever. That’s why we’re excited to announce that the Cyberhive Matrix Q1 20...
Labyrinth Security Solutions Announces Strategic Partnership with IITD
Zabrze, 4 Feb 2025 Labyrinth Security Solutions, a leader in innovative deception technology for network monitoring and threat detection, is pleased to announce a new distribution partnership wi...
LABYRINTH Deception Platform Supports Proxmox
Exciting News: LABYRINTH Deception Platform Now Supports Proxmox! We’re thrilled to announce that starting from version 2.1, the LABYRINTH Deception Platform (LDP) now fully supports Proxm...
Mind-Info Kft. Becomes Labyrinth VAD Partner in Hungary
Labyrinth’s team is pleased to announce that Mind-Info Kft. became our Value-Added Distributor (VAD) in Hungary. This strategic partnership will enhance the delivery and support of Laby...
Labyrinth Security Solutions Sponsors KKS Tarnowskie Góry: A Commitment to Excellence On and Off the Court
We are excited to share some fantastic news with our community—Labyrinth Security Solutions is now a proud sponsor of KKS Tarnowskie Góry, a spirited and talented team competing in the...
Labyrinth joins the Cybersecurity Made in Europe club
Our team is excited to announce that as the Finalist for the ECSO CISO Choice Award 2025, Labyrinth receives ECSO label ‘Cybersecurity Made in Europe’. The primary go...
Labyrint is among the First Finalists for the ECSO CISO Choice Award 2025
We have fantastic news to share: Labyrinth is among the finalists of ECSO's CISO Choice Award in 2025! Our colleague, Anastasiia Dorosh, Cybersecurity Implementation Team Lead at Labyrinth, ...
Let’s meet at the 2024 London Infosec conference!
Labyrinth is thrilled to announce, that we are participating in the London Infosec Europe conference on 4th - 6th of June. Infosecurity Europe is a premier event in the European IT security indu...
Looptech Becomes Labyrinth’s VAD Partner for Middle East
Labyrinth is pleased to announce a partnership with Looptech, a Value-Added Distributor over GCC Countries and Middle East, with prominent experience in cybersecurity field. The primary aim of L...
Labyrinth Partners with SecureVisio (eSecure Sp. z o.o., Poland)
We are delighted to announce partnership with SecureVisio, an automated cybersecurity and risk management platform. SecureVisio supports enterprise, public, SMB clients as well as SOC environments....
Release notes v2.0.55
1. NEW AND IMPROVED 1.1. Improving the Dashboard More interactivity has been added to the Dashboard. Now you can click on any dashboard element and go to the corresponding lists w...
Utilizing Deception Solution in the Implementation of SOC for Galnaftogaz - IT Specialist
Our partner, IT Specialist, Ukrainian company providing professional IT and cybersecurity services recenly published insightful case study about Labyrinth Deception Platform usage i...
A1 Becomes Labyrinth’s VAD Partner in Slovenia
The Labyrinth team is excited to announce a partnership with A1 Slovenia, a Value-Added Distributor (VAD) in the Slovenian region, offering business clients premium solutions in cybersecurity, IT a...
Labyrinth and COMGUARD a.s. Partnership Announcement
We are thrilled to announce that Labyrinth Security Solutions sp. z o.o. and COMGUARD a.s., a leading B2B Value Added Distributor, specializing in safeguarding data and communication, as well as ma...
Labyrinth partners with Energy Logserver
We are very pleased to announce a technology partnership with the manufacturer of the Polish Energy Logserver modular platform, providing LogManagement, SIEM and SOAR technologies. Over ...
Release notes v2.0.54
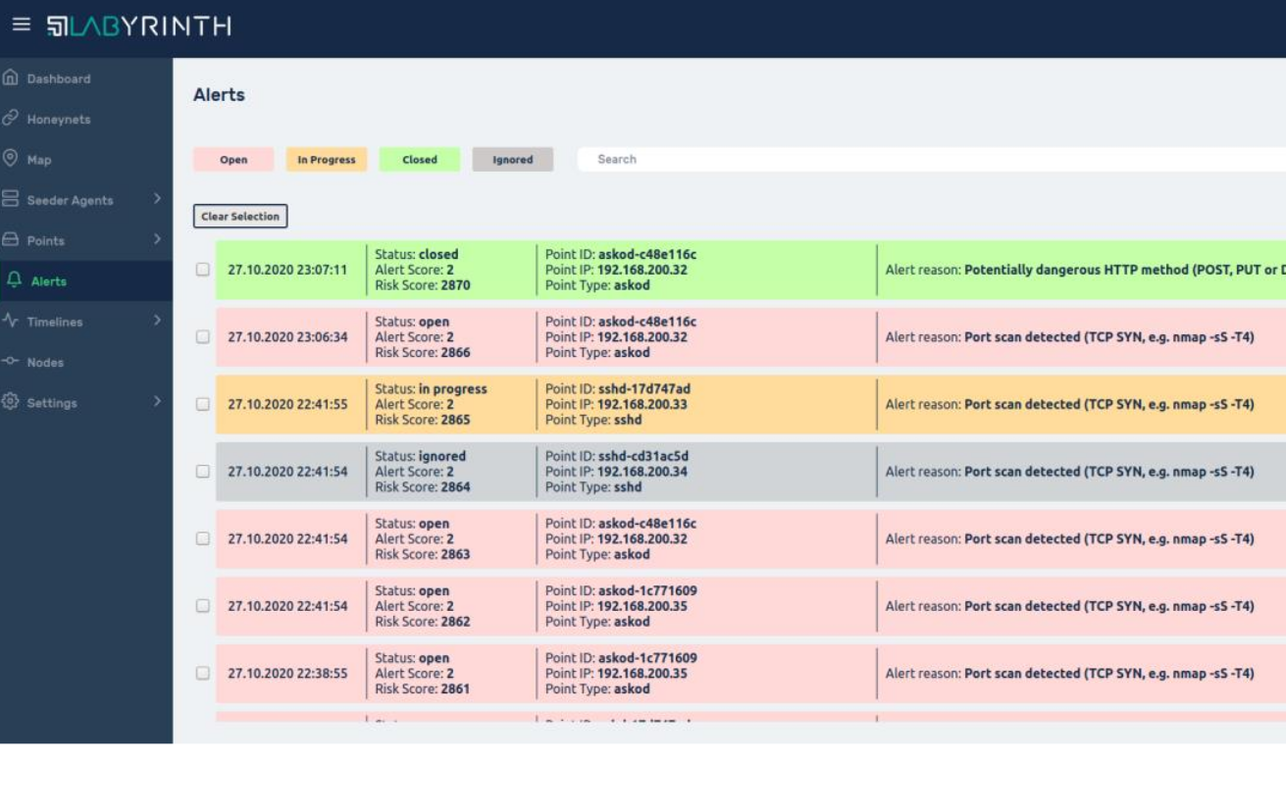
1. NEW AND IMPROVED 1.1. Improved Alerts representation One of the biggest changes of this release is the way we operate with Alerts. The scope includes the following: 1....
Labyrinth Forges Strategic Alliance with UnderDefense for Cybersecurity Excellence
Labyrinth and UnderDefense are excited to announce their innovative partnership that combines Labyrinth’s exceptional team of cybersecurity experts with UnderDefense’s Security-as-a-s...
Labyrinth Announces EMEA Channel Chief
Zabrze, 17th October 2023 - LABYRINTH SECURITY SOLUTIONS, an expert cybersecurity company specializing in top-notch deception technology, is thrilled to announce a significant addition to its exe...
Release notes v2.0.53
1. NEW AND IMPROVED 1.1. API for interaction with Labyrinth Deception Platform We added a REST API to obtain the necessary data when working with Labyrinth Deception Platform. Cur...
Cybersecurity in Wartime: Challenges for the State and Business
Our colleague, Yuriy Gatupov, Labyrinth's CCO, participated in the panel discussion "Key lessons for companies' security" at Lviv IT Cluster's conference, which was ...
Labyrinth partners with Incident Busters Forum 2023
On June 21-22, 2023, Labyrinth had the pleasure of participating in the first edition of the Incident Busters Forum event in Warsaw, where there were lectures, discussions, a decision-making game...
beyond SSL and Labyrinth: more security for your company
beyond SSL GmbH and Labyrinth Security Solutions have created an alliance of their “SparkView” and “Deception Platform” technologies to provide even more securit...
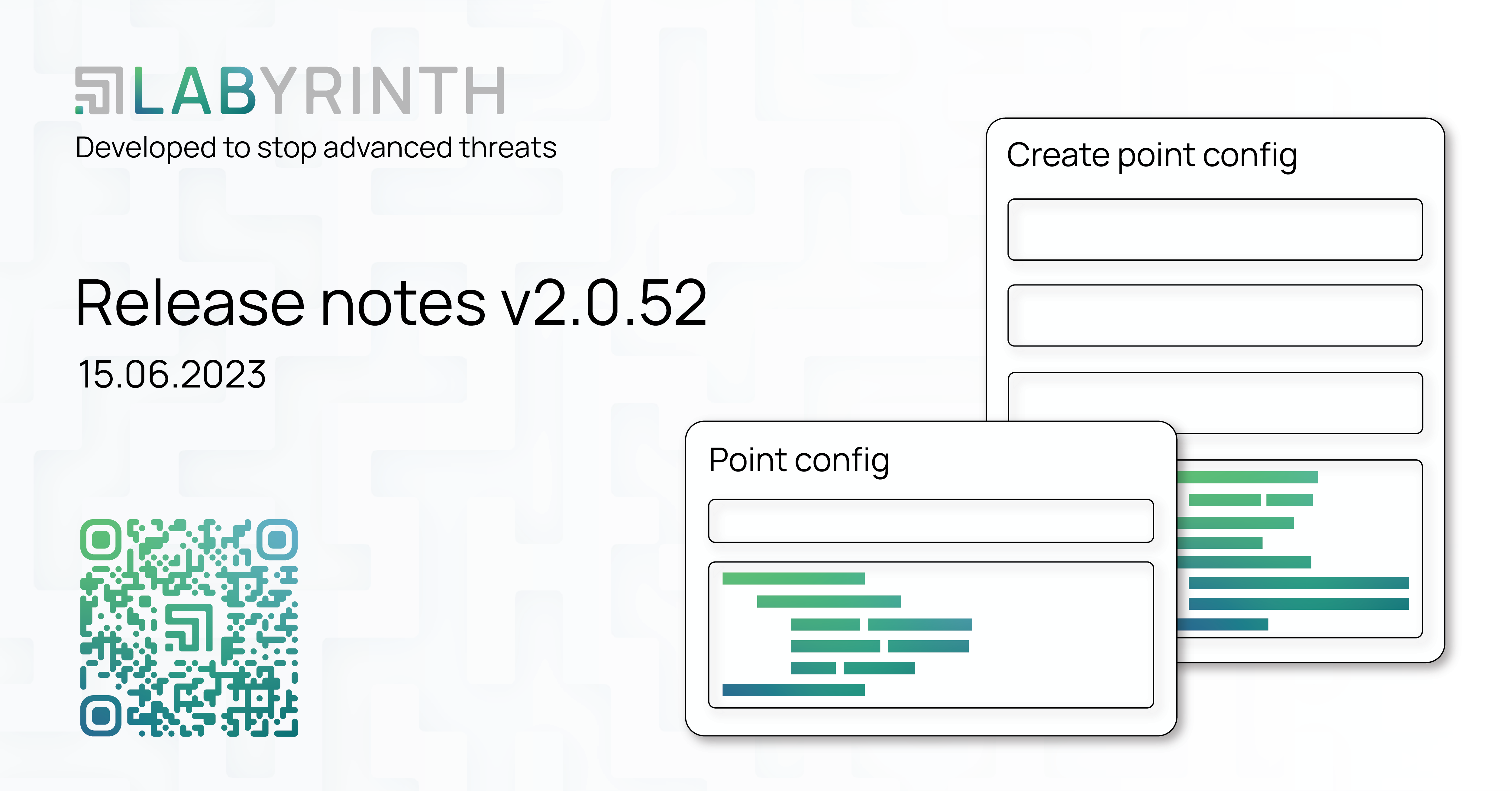
Release notes v2.0.52
1. NEW AND IMPROVED 1.1. Customization of Points settings This release has become an impetus for further development in expanding the number of parameters for customizing the Points that will be ...
Labyrinth and ALESTA Partnership Announcement
Labyrint's team is happy to announce our new partnership agreement with ALESTA, a well-known Ukrainian system integration company. ALESTA is a modern system integrator aiming its efforts...
Labyrinth Joined Partnership for Cyber Security Innovation (PCSI)
The Labyrinth Development team is honored to announce joining The Partnership for Cyber Security Innovation (PCSI) as a Laison Partner. PCSI is a public-private alliance performing a fundamental f...
Release notes v2.0.51
1. NEW AND IMPROVED 1.1. Integrations: Crowdstrike The integration allows you to: Enrich the alert with data about the host from which the attack was launched based on the alert's Source IP;...
Labyrinth is a new ECSO member
We are glad to announce that Labyrinth is a new European Cyber Security Organisation (ECSO) member. ECSO's main objective is to support all initiatives to develop, promote and encourage Europe...
Release notes v2.0.50
1. NEW AND IMPROVED 1.1. Improved Honeynet list Honeynet list was refactored, which includes: New pagination Filtration Data download in CSV format 1.2. Description of a re...
Labyrinth and Emplos Partnership Announcement
We are proud to announce our first partnership in the Baltic countries with Emplos LTD. Emplos LTD is an IT systems integrator with an impeccable reputation, which offers its customers innovat...
We are welcome TIVA
Our partner network is growing - we are welcome TIVA, the company that specialized in design, construction, and integration of security systems. The main mission of the company is to create specia...
Release Notes 1.3.5
Feature list New timeline on the dashboard With the help of the new dashlet, an operator can quickly get visual information about the level of malicious activities in a given period of ti...
Release Notes 1.3.4
Feature list The new dashboard This release introduces a significant redesign of the dashboard. Now the system operator can choose a time period and the information for the desired period wi...
Amind Partnership Announcement
We are glad to announce that our partner network was enhanced by new system integrator – Amind! This strong technical collaboration will help our customers to get even more benefits out of La...
Release Notes 1.2.3
Features list The manual mode of point types distribution in Honeynet Prior to this release, the choice of point types and the number of points to generate was carried out fully automatically...
Labyrinth and Netwave Partnership Announcement
We are proud to announce our new partnership with Netwave for the promotion of Labyrinth Deception Platform that allows organizations to implement network detection and response (NDR) solution to d...
Release Notes 1.2.0
We are excited to announce that the newest version of Labyrinth Deception Platform is here! This release is full of new features that provide our users with more attack visibility, more convenient ...
New Partnership Announcement
We are welcome our new partner - CS Consulting! The company has over 10 years of experience in consultancy and implementing innovative solutions in the field of information security, data backup, a...
Cybersecurity - Protecting Business, Protecting the State
Our team took part in the third international forum "Cybersecurity - Protecting Business, Protecting the State". After long months of COVID break, it was a great pleasure to meet so many ...
Octava Cyber Defence
We are excited to announce the start of our partnership with one of the leading Ukrainian MSSP providers – Octava Cyber Defence! We believe that this help to enhance Octava’s secu...
SWG Graduation certificate
We are proud to announce that our team has successfully finished the Startup Wise Guys 7 week Online Pre-acceleration program. What a journey this has been! Thank you, Startup Wise Guys team, for t...