
26Jul
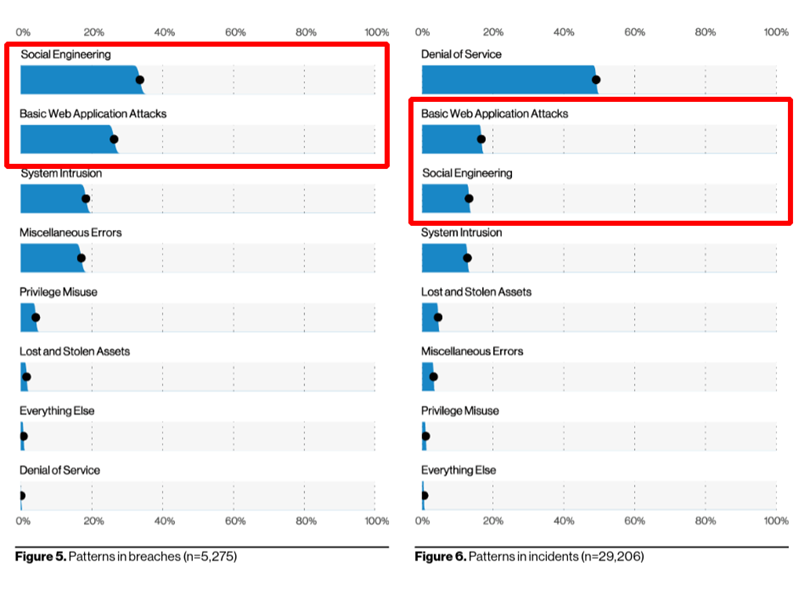
The Summary of Findings in the recently published 2021 Data Breach Investigation Report shows that Web Applications Attack is the second most commonly used approach leading to both, breaches, and incidents https://www.verizon.com/business/resources/reports/dbir/ (according to Verizon: Breach - an incident that results in the confirmed disclosure—not just potential exposure—of data to an unauthorized party; Incident - a security event that compromises the integrity, confidentiality or availability of an information asset).
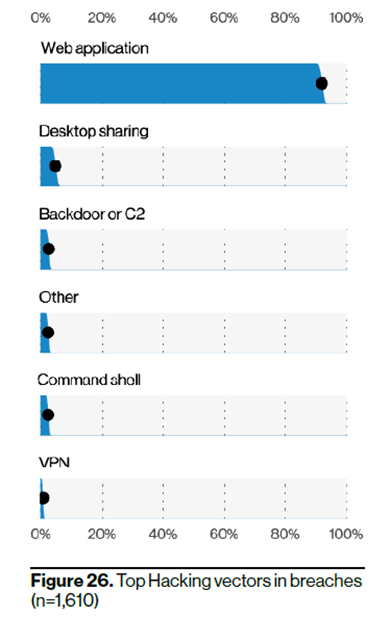
Moreover, the authors of the report highlights Web application vulnerabilities exploitation as the most used by hackers attack vector resulting in breaches.
“Another noteworthy change this year is the increase in rank of Desktop sharing as the vector of a Hacking action to second place. As Figure 26 demonstrates, it is completely overshadowed by Web application as the attack vector.” – stated in the report.
To address a web protection needs, Labyrinth Deception Platform has embedded a unique technology - Universal Web Points. Such kind of decoy allows to provide an additional leer of security for Web based applications and services. The Platform automatically discovers and creates emulations of any web applications in a local network (web services, web interfaces, and even Web APIs). For example, Universal Web Point faithfully imitates web interfaces of network devices, different applications administrative consoles, mail server or CRM interface, etc. At the same time, it will be extremely difficult to distinguish where is the real web application, and where - its imitation. In addition, Universal Web Point not only fully reflects the “original” web interface, but also contains vulnerabilities, which makes the imitation more attractive for attackers.
Our Platform provides security teams with an efficient yet simple tool for the earliest possible detection of advanced cyber threats that have bypassed traditional security systems. Labyrinth detects threats without continuous network monitoring and producing tons of data and without specific knowledge needed to work with the solution.

